5 Ways ICT Solutions Can Streamline Your Business Operations
Source: Freepik Efficient business operations are key to staying competitive. ICT (Information...
The Cloud: Redefining Endpoint Security
The cloud has emerged as a fundamental component for businesses looking to...
Revolutionizing Business Operations: The Impact of IT Consultation
In an era where technology is rapidly evolving, staying ahead of the...
How to Avoid Phishing Attacks: A Comprehensive Guide
Recently, phishing attacks have become increasingly sophisticated and prevalent. Cybercriminals use phishing...
Understanding Intrusion Detection Systems (IDS) in Network Security
In today’s digital age, where cyber threats are increasingly sophisticated and prevalent,...
The Ultimate Guide to Endpoint Security: Protecting the Digital Frontier
In today’s interconnected world, endpoint security has emerged as a critical component...
The Cloud’s Silver Lining: Revolutionizing Storage in the Digital Age
Data has become the lifeblood of organizations across industries. From small startups...
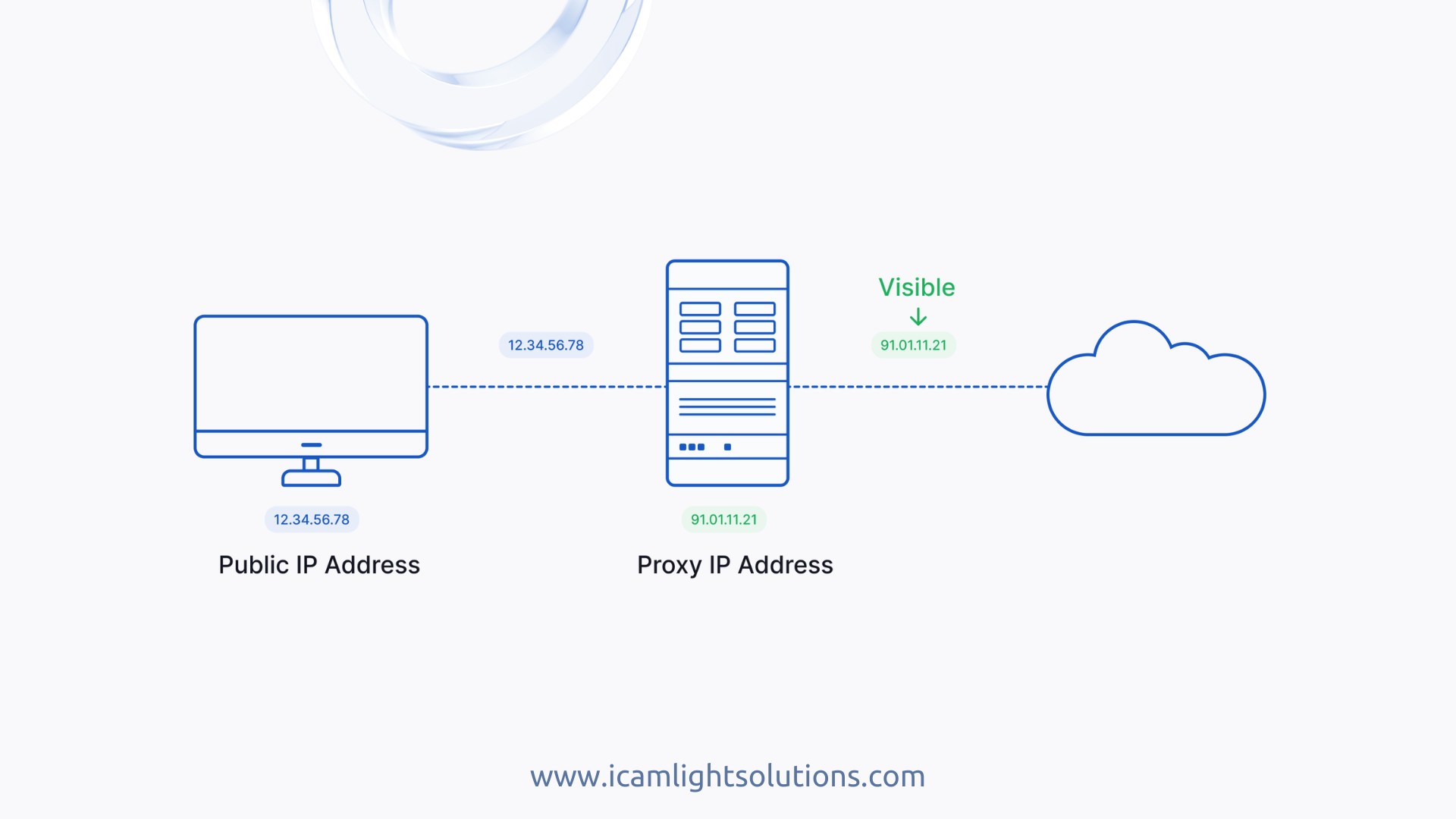
Navigating the Web with Proxy Servers: A Closer Look
In the vast expanse of the internet, there’s a hidden network of...
Strengthening Your Business Fortress: The Vital Role of Firewalls in Securing Data
In today’s digitally driven world, where businesses thrive on data, safeguarding sensitive...
Navigating the Challenges: Unraveling the Fallbacks of 5G Technology
Introduction: In the fast-paced world of technological evolution, 5G has emerged as...